Software Demonstration Video


To perform any file related operation, user needs to authenticate himself via fingerprint scan. If fingerprint authentication is enabled by Sender, then receiver can access the encrypted docs by verifying his fingerprint...
READ MORE....
To perform any file related operation, user needs to authenticate himself via Iris scan. If Iris authentication is enabled by Sender, then receiver can access the encrypted docs by authenticating his iris...
READ MORE....In case the Sender wants his docs to be accessed in a particular region, he can do so by Setting up Lat, Long Coordinates of that location. Sender will encrypt the docs using X-Encryptor tool & will enable ...
READ MORE....
At VCrypt Systems, we believe in creating a long term relationship with each of our customers. We offer excellent pre-sale, on site and after sales support for the products that you buy from us. Rest assured to get all the help and information that is required by you in relation to any purchase made with us...
LEARN MOREVCrypt Universal soft license key is free for non-commercial uses. Universal key already integrated within VCrypt X-Encryptor & Application launcher tool. User can encrypt data with universal key and apply Two-Way Authentication to enhance the security level and share data to other users.
It works on specific PC & is specific to the software(s) also which is configured in the license key. The motive behind owning a license is to avoid the software from getting copied, shared or illegally used (casual piracy) by non-licensed users thus increase the revenue.
It works on individual PC & is specific to the software(s) also which is configured in the license key. It's not bound to a particular PC. Advantages are the portability, as well as the access to easy licensing for integrators and support technicians who may need to move from location to location to offer support on the go.
READ MORE....
Developer

Developer & Sales & Marketing

PHP Developer

UI Developer

Tester

Graphic Design

Sales

Tester
VCrypt is a complete holistic security suite which can bring breakthrough in data security
by providing a hack proof mechanism
solutions
Ability to develop common/inhouse encryption algorithms
Ability to add various layers of security to ensure authorized access like OTP/PC/HDD/Network
Ability to update encryption mechanism/policies from time to time
How Piracy Works
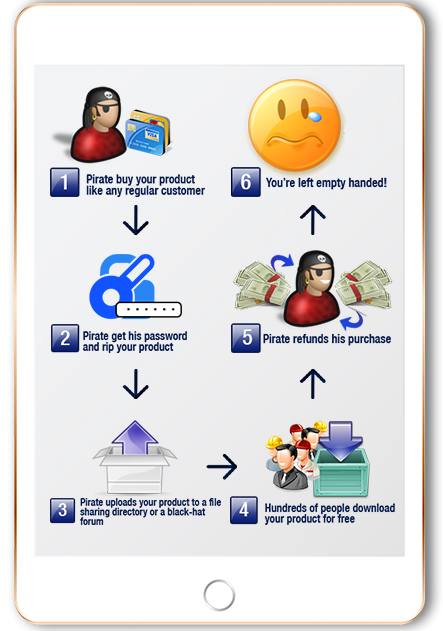
solutions
Ability to implement common/customized security policies
Ability to add biometrics security like finger print/IRIS scan
Ability to run/play/read/write data without decryption at disk level